
5 Tips to Secure Data for the Enterprise
Enterprises that underestimate the guile of cybercriminals are facing an existential threat. The rise of cybercrime over the last decade is staggering, and it’s more

Enterprises that underestimate the guile of cybercriminals are facing an existential threat. The rise of cybercrime over the last decade is staggering, and it’s more

It seems that every day a new story breaks about another business falling victim to ransomware. Even if organizations are aware of the risks, there

Organizational workflows depend on synchronous communication tools that connect your entire workforce regardless of geographic location. A secure communications and collaboration plan helps align your

Cybercriminals aren’t slowing down and today’s organizations need a proactive approach to secure their communications. Business email compromise (BEC) exploits companies to financial risks and
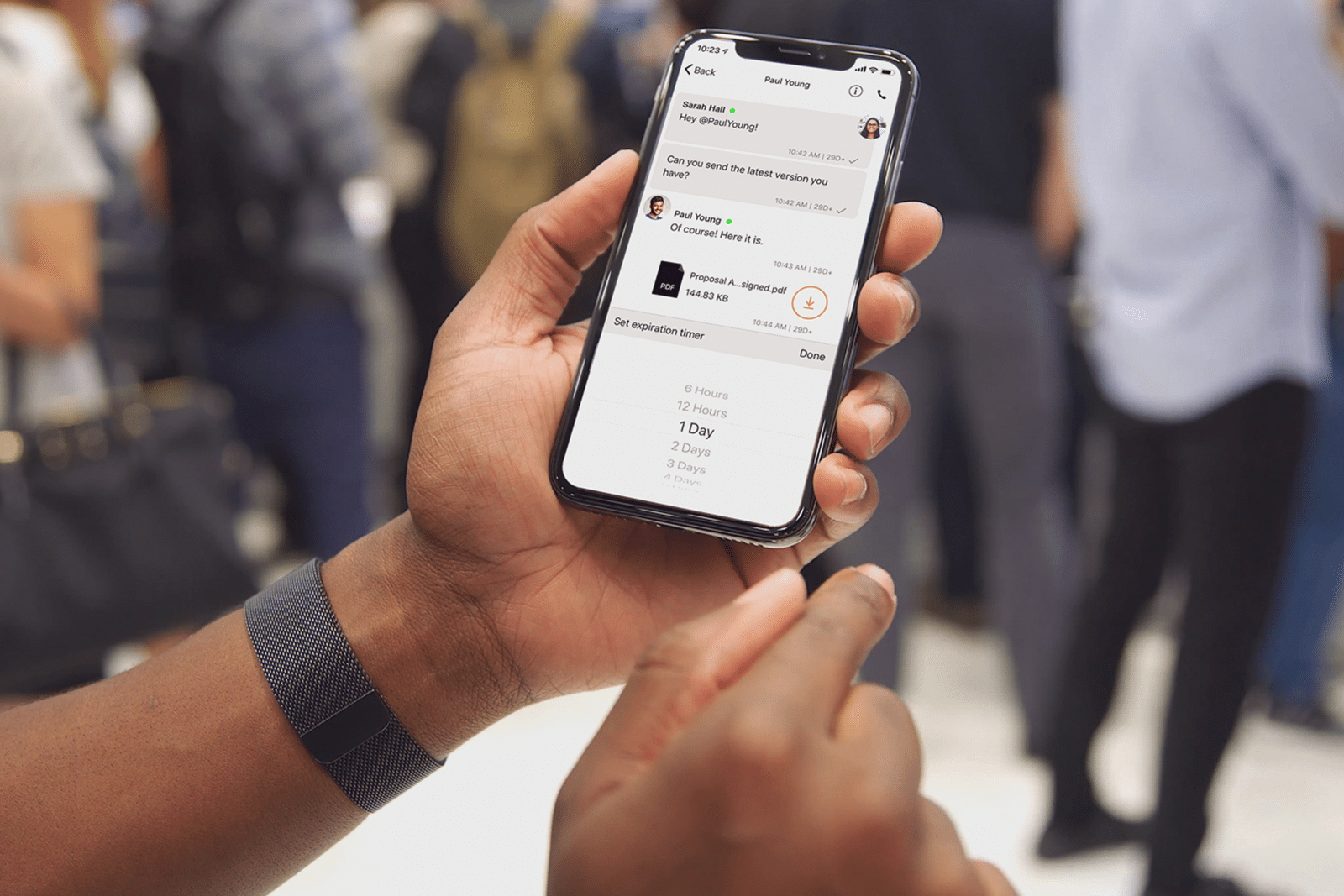
From individual private messaging to DoD-approved communication for the Military, Wickr has a solution to fit everyone’s secure collaboration needs. See the infographic below for

The cost and damage a data breach wreaks on enterprises is often ambiguous, and you will only understand the real impact way down the line.

You cannot risk your entire enterprise by leaving the doors to your building open after hours. Similarly, the need to encrypt and secure your data

Ransomware is a type of malicious software that invades computer systems and encrypts key data. Attackers demand that victims pay a ransom in order to

Due to the COVID-19 pandemic, more and more employees are working from home – and remote collaboration presents a unique as well as ongoing set

Many organizations today are sharing information about cybersecurity threats, vulnerabilities, and solutions. On the surface, this sounds like a good idea – you learn more

You might think that the data you receive via your cellphone network is safe and secure. You’d be wrong. Recent research reveals a flaw in

The SolarWinds hack was a major attack that affected thousands of companies as well as multiple government agencies. The size and nature of the attack

End-to-end encryption (E2EE) is a system of secure communication, protecting data so that only the sender and the receiver can read the message. If the

On July 2, 2021, the IT solutions provider Kaseya announced that it had become the victim of a massive ransomware attack. The Kaseya attack ultimately

Ensuring cybersecurity compliance is challenging. You need to decipher all the regulatory acronyms and understand all the governmental and industry regulatory requirements. You also need

A growing number of enterprises are turning to end-to-end encryption to secure their data and communications. End-to-end encryption, also known as E2E, builds on traditional

Threat intelligence involves collecting, analyzing, and disseminating data about malicious actors, their behavior, and their methods. This information is then used to strengthen an organization’s

More than 4 billion people worldwide use email. While email is exceedingly popular, it is one of the least secure ways to communicate on the Internet today.