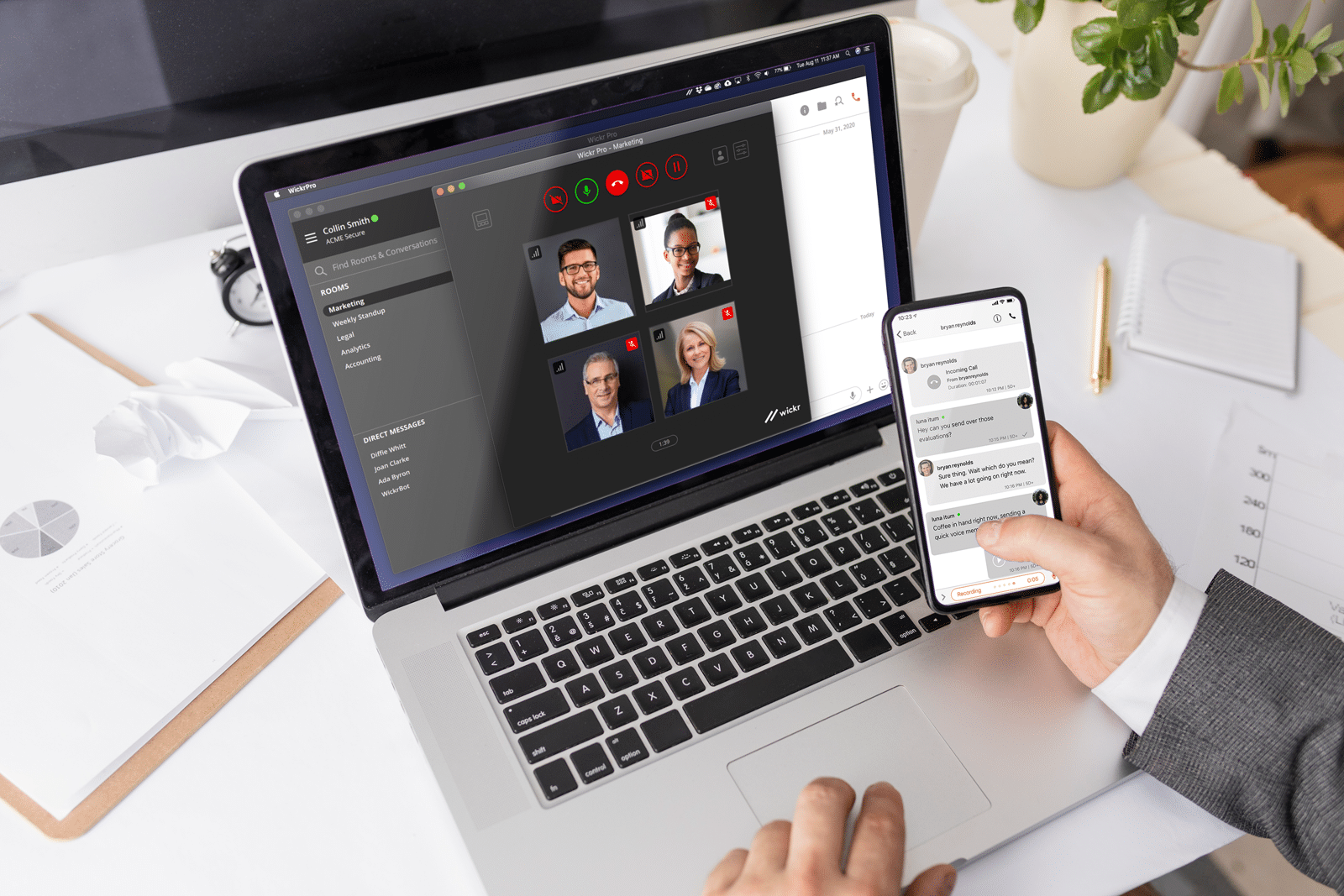
Our focus on end-to-end encrypted enterprise communications
At Wickr, we’ve served a diverse set of customers that range from the boardroom to the battlefield. Since AWS acquired Wickr in 2021, we’ve listened

At Wickr, we’ve served a diverse set of customers that range from the boardroom to the battlefield. Since AWS acquired Wickr in 2021, we’ve listened
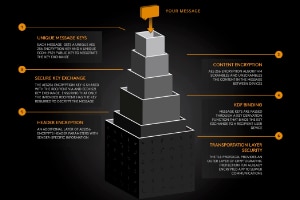
The Wickr Secure Messaging Protocol provides a platform for secure communications. This White Paper describes a method for sending messages with a set of security

There are hundreds of US federal government departments and agencies. The vast majority are subject to Federal Records Act (FRA) and National Archives and Records

More and more, CISOs are turning to the quantification of cyber risks versus deployed controls to demonstrate the ROI of cybersecurity programs. The increase in

As humanity marches unflinchingly toward the future, we need to anticipate the impact that emerging technologies will have on our society. Ethical concerns surrounding data

After months of marking up a dozen spending bills, legislators have finalized the cybersecurity budget for the fiscal year 2023. The collective set of bills

Wickr RAM (Recall, Alert and Messaging) is now available to the U.S. Department of Defense (DOD) through Cloud One, which is a cloud hosting infrastructure and

With the world’s organizations and government agencies turning to digital technologies for all operations, the need for secure collaboration is at an all-time high. End-to-end

Maintaining information security within an organization without impeding operational efficiency requires a secure communications strategy for all business processes. Building workflows with end-to-end encryption (E2EE)

The magnitude of data-driven operations that organizations rely on will only increase with time. Having a clear and effective encryption strategy for 2022 is paramount

Distributed computing is on the rise, especially with the growth of the remote workforce. Unfortunately, distributed computing presents an enhanced security risk that requires a

Have you seen images of warfighters looking at chest-mounted smartphones or tablets, and wondered which application they’re using? Chances are, it’s ATAK. The Android Team

Enterprises have to improve their security posture and ensure compliance with data privacy legislation as part of their core mandate. The use of digital and

When you consider the rapid rise of digital operations across the public and private spectrum, government agencies face the same challenges as every modern business.
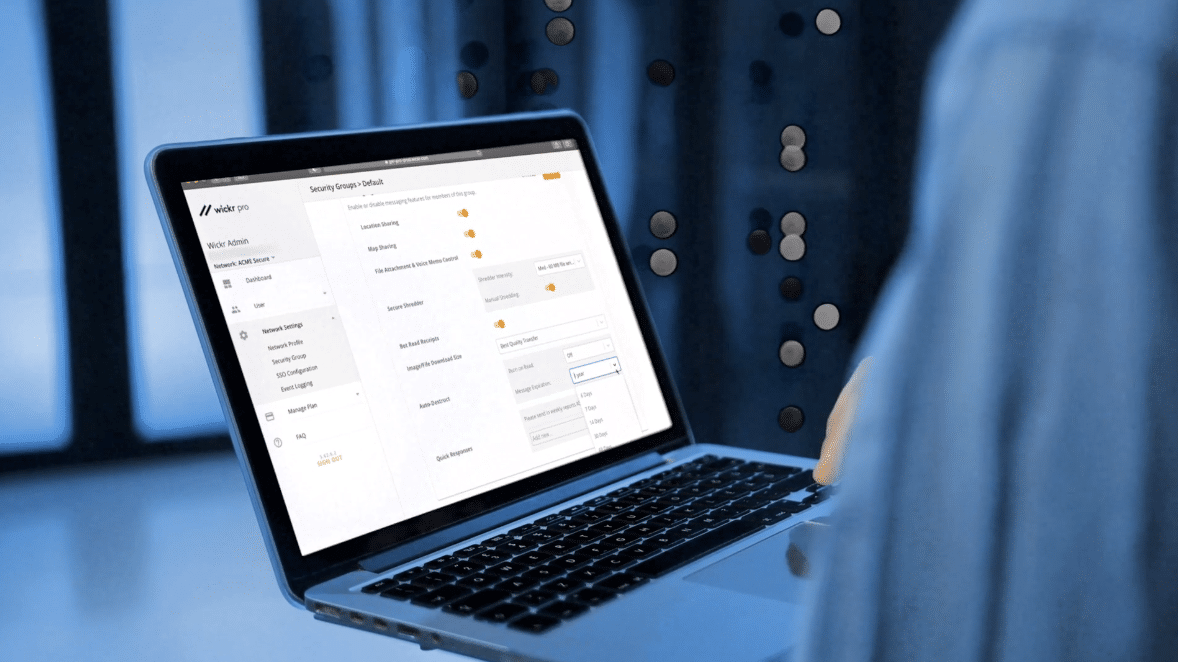
Did you know that 91% of organizations have been victims of web and mobile based cyber incidents? Or that 69% of businesses were hit by ransomware attacks

Secure distributed data storage is the wave of the future for corporate IT. It’s all about spreading the risk by storing data across multiple servers.

Unified communications (UC) involve the integration of multiple enterprise communication tools into a single interface. This typically includes voice calls, instant messages, video conferences, and

Enterprises need to fully secure their important data and communications. While there are many cybersecurity approaches and tools available, an increasing number of enterprises are